When Danish craft brewer Mikkeller decided to open a Copenhagen brewpub in conjunction with Indiana brewer 3 Floyds, the company quickly decided to look for a location in Kødbyen, the city's historic meatpacking district.
"There was no doubt in Mikkeller's mind that this was the area," says Kamilla Hannibal, event and communication manager for the recently opened brewpub, which serves beer and American-style barbecue under the name WarPigs. "For this place, it was quite a natural choice because of its location, but also because of its reputation."

Mixing Business With Pleasure
Not that long ago, Kødbyen was an isolated hub of industrial-scale butcher shops, slaughterhouses, and food wholesalers, seldom visited by residents without some sort of ties to the industry. But the neighborhood has recently seen an influx of trendy art galleries, co-working spaces, bars and restaurants. Tourists are increasingly drawn to the area to visit businesses like Tommi's Burger Joint, a kind of Icelandic answer to Shake Shack, and Jolene, a dance club named after the Dolly Parton song.
As some traditional butchers and meatpackers have migrated outside of the city, the transformation of the neighborhood has drawn natural comparisons to the now uber-chic Meatpacking District on Manhattan's West Side, where landmark status preserved many old buildings but not the old businesses.
"Greenwich Village had been a fashionable district for some time, but the [adjacent] Meatpacking District was not, until about 15 years ago," says Andrew Berman, executive director of the Greenwich Village Society for Historic Preservation.
Berman's group successfully pushed for official designation of the Gansevoort Market Historic District, which since 2003 has granted landmark status to much of the area's central core, limiting the scale of new construction and preserving hundreds of historic buildings.
Before that time, Manhattan's Meatpacking District was essentially off most New Yorkers' radar. Similarly, Kødbyen "was not part of the mental map of an average citizen in Copenhagen," says architect Serban Cornea, a partner in the firm Mutopia, which was commissioned by Copenhagen's municipal government—which owns the district's real estate, leasing it to businesses—to help plan Kødbyen's future.
Mutopia and city officials worked to balance the needs of the traditional businesses—which need places to drive and park delivery trucks through the neighborhood—and new businesses, which were reliant on safe walkways and bicycle routes as well as areas for outdoor dining. For reference, Cornea says they looked at transformed historic quarters in cities around the world, including New York's Meatpacking District.

Where's the Beef?
New York's Meatpacking preservation effort focused on the architectural details of the historic neighborhood, some of which dates to the mid-19th century. "The key to the Meatpacking District is that it preserves the old cobblestone streets and some of the key older buildings, but allows them to be renewed and reinvigorated," says Mitchell Moss, a professor of urban policy and planning at New York University and an expert on New York City development. "The greatest success was the conversion of the Western Beef store to the Apple Store," says Moss, referring to a landmarked building on West 14th Street that once housed a discount wholesale and retail supermarket before being renovated to sell iPhones and Macs.
A former Nabisco plant now hosts mostly upscale food and retail vendors as Chelsea Market, and shoppers can dine on macarons, gelato, and Thai curry at Gansevoort Market, once a bustling wholesale meat market.
New construction associated with the Meatpacking District, like the chic Gansevoort and Standard hotels and the soon-to-open new home of the Whitney Museum of American Art, has been restricted to areas outside of the landmarked area, especially along Ninth and Tenth avenues and the High Line elevated park. "Outside of the designated [historic] district but still within the neighborhood there's been some pretty dramatic changes," says Berman.

There's regret over the migration of long-standing meat and produce businesses from the Meatpacking District as well as other downtown neighborhoods. "At one time we had cheese and eggs down at Washington Street, and we had meat down at Gansevoort," says Moss, noting that over time the vendors all moved to the Hunts Point area of the South Bronx. This was thanks to the advent of refrigerated trucking, which meant it wasn't necessary to slaughter and butcher animals close to where they would be consumed.
To Berman, relying on trucking is a loss for the city in terms of environmental considerations—meat and other goods now have to be transported from the Bronx through Manhattan—and in terms of economic diversity. "Certainly we would have liked to have kept many more of the meatpacking businesses there or have more market-related uses there," he says. "So much of Manhattan has skewed to the high end of the socioeconomic spectrum and towards jobs that are either very high-end jobs or service industry jobs that serve people at the high end."
But New York's preservationists and planners are limited to working with the city's zoning code, and, in a developer-driven real estate economy, that's ultimately a blunt instrument, says Berman. The area is generally zoned for light industrial use, which allows everything from actual meatpacking to high-end office space, he says. "Hotels, offices, and things like meatpacking plants are all the same category of use under the city's zoning regulations, so you can't allow one without allowing the other in a district like this."
There Will Be Blood
Officials in Copenhagen have taken a different approach to the renaissance of their city's old meatpacking quarter. While visitors to the New York district's boutiques and nightclubs would be unlikely to stumble upon a functioning abattoir, Copenhagen has taken pains to make sure Kødbyen still has room not only for its distinctive pre-war buildings but also for its traditional businesses.
"In the morning, you see butchers in white coats with blood on their hands walking around the streets of the meatpacking district," says Jakob Munk, a partner and brand director at Kødbyen's Butchers and Bicycles, a bike maker based in what was a 19th-century stable turned falafel factory. "During the day, the people in the meatpacking district slowly change from butchers in white suits to hipsters with beards and hats on their bikes."
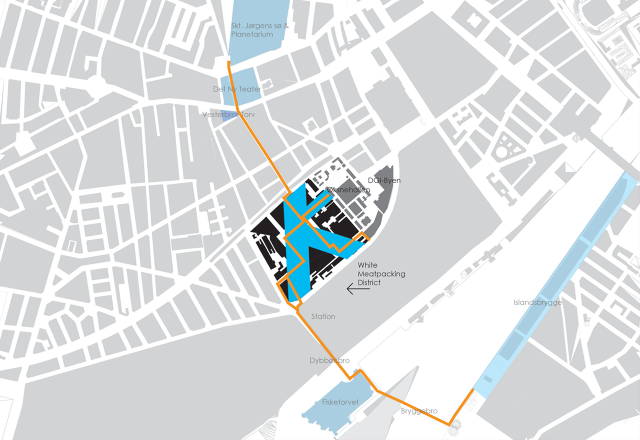
Mutopia's plan, first released in 2007, came to be known as the "K-plan," both for the neighborhood's initial and the shape of the transportation routes through the area. The plan carefully considers parking and traffic for both businesses and pedestrians.
"What we did was a number of different things to organize time slots for the parking of the big trucks, the big vehicles, and using the in-between time slots which were available to organize and support the implementation of temporary activities within these areas," says Cornea. "Part of the heavy traffic has been moved from a strategic area, which is the probably the most interesting in terms of sun exposure, to make the space available for cafes and outdoor life."
As in New York, the city also set rules for preserving the interiors and exteriors of buildings in the area, particularly in the White Meat District, about 12 acres of glistening 1930s-modern structures seen as part of the city's cultural legacy.
"There's still a lot of restrictions on what you can build and what you can change, since they want to preserve that look," says Hannibal, explaining WarPigs will be in a former butchery in the White Meat District. "We still have the hooks in the ceiling where the carcasses used to hang from the ceiling, and all the walls are proper butchers' walls that are easy to wipe."
Butchers and Bicycles also made few changes to the space it took over in 2013, says Munk—besides spending about 12 hours power-washing years of caked-on fry oil off the walls. "It was kind of messed up in a way that only a falafel factory can be messed up," he says. The newly degreased tile walls and historic architecture help attract visitors to the space, and the diverse environment keeps the company's bike designers inspired, says Munk. "It influences our creativity," he says. "It gives us a lot of energy to come down to our really cool showroom, and it's also a workshop."
Munk was happy to see a nearby longstanding food wholesaler sign a new 15-year lease.

The new district plan would add some new mixed-use retail, office, and residential buildings to less-dense parts of the neighborhood and add roof gardens to some of the existing structures. A second phase of Mutopia's plan, called Kødbyen 2025, was released in 2013 to plan for the neighborhood's continued evolution.
Longer-term planning is more feasible in Copenhagen thanks to greater city government control, whereas market-driven New York is characterized by relatively rapid changes in its urban environment. "I think anyone who says they can predict what New York would be like in 10 or 15 years is kidding themselves," says Berman. For example, the Whitney Museum's relocation to the Meatpacking District from the Upper East Side is a move that no one would have predicted 20 years ago.
As the landlord in Kødbyen, the city can take a more hands-on approach to shaping its meatpacking neighborhood into the ideal mix of business and pleasure, but don't expect it to happen in a New York minute. Comparing her home to New York, WarPigs' Kamilla Hannibal admitted, "Everything moves incredibly slow in Copenhagen."